Recently in the world of data and analytics, life was disrupted by a sophisticated referral spam attack, originating from Poland around February 14th, 2024. Leveraging deceptive domains such as news.grets.store and static.seders.website, this campaign has posed significant challenges for digital marketers and website owners worldwide. Thisarticle aims to dissect the nature of this attack, its implications, and introduces an effective countermeasure through Google Analytics 4 (GA4).
The Attack Unveiled
The latest referral spam campaign cleverly simulates traffic from seemingly reputable sources, leading users to malicious websites. It’s crucial to note: do not visit these links. The attackers have employed a form of gtag hijacking, using GA4 Data Stream IDs on their pages to mimic legitimate site traffic. This sophisticated tactic was uncovered with insights from the online community, revealing that traditional defenses like IP blocking and .htaccess modifications are ineffective against this type of spam.
Origin and Discovery
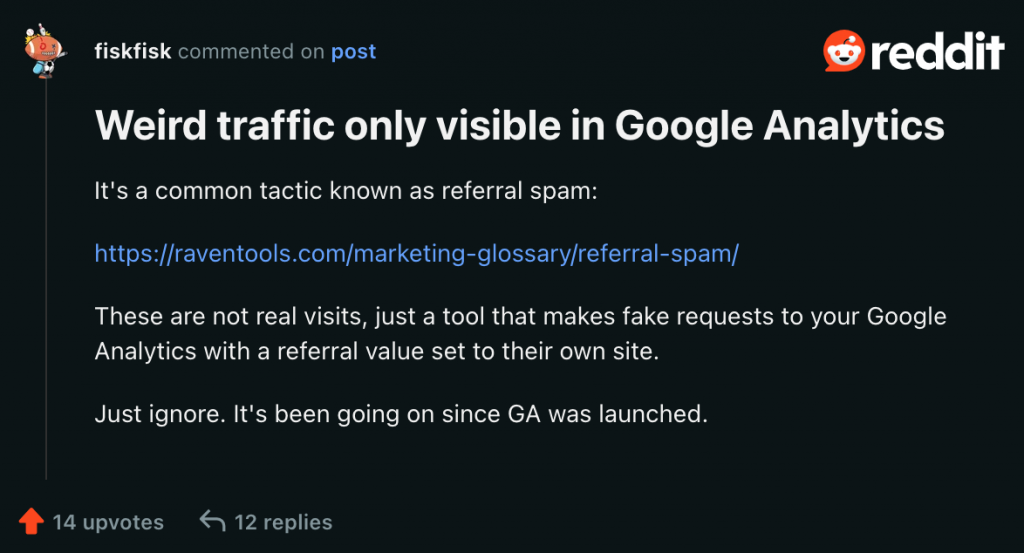
Originating from Poland, the attack began around Valentine’s Day, 2024. The pivotal breakthrough in understanding the mechanism behind this sophisticated referral spam came from the digital marketing community, through both a detailed discussion on Reddit and insights shared on a Google help thread. A user in the Reddit thread highlighted, “These are not real visits, just a tool that makes fake requests to your Google Analytics with a referral value set to their own site.”
We’ve seen similar patterns where the GA4 ID is hijacked and used elsewhere, making traditional blocking methods ineffective. Similarly, the Google help thread provided further evidence of the attack’s origins and its impact on analytics data. These insights were crucial in revealing why conventional methods, such as IP blocking and .htaccess modifications, have been unable to thwart the spam traffic effectively.
Impact on Businesses
The influx of fake data from this attack disrupts website analytics, leading to potentially flawed marketing insights and decisions. Businesses find themselves diverting valuable resources to filter out the noise, while also facing increased security risks from engaging with these spam referrals.
Strategies for Defense
Our primary defense strategy against this referral spam attack is a crucial adjustment within Google Analytics 4 (GA4): the configuration of cross-domain settings. By configuring these settings to only recognize traffic from verified domains, we effectively block malicious referral spam. Our targeted approach preserves the integrity of your analytics data, ensuring that your marketing strategies are based on accurate and meaningful insights. For step-by-step instructions on how to configure these settings, Google provides a comprehensive guide: Configure cross-domain measurement.
As this discussion continues, we may update this post based on results and the dynamic topic.
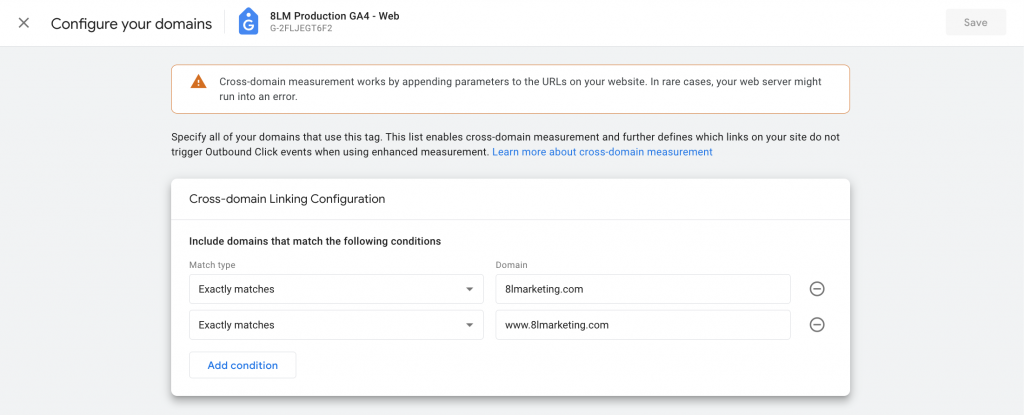
Please update to match your expected domains to measure traffic from
Conclusion: A Call to Vigilance
The referral spam attack from Poland underscores the evolving challenges in digital security and data integrity. By adopting a focused defense strategy, such as configuring the cross-domain settings in GA4, we can protect our digital landscape against these insidious threats. This incident serves as a reminder of the importance of staying informed and proactive in our security measures, ensuring our digital marketing efforts are grounded in reliable data.
Edit / Update 1:
The day this original post was published, we implemented the crossdomain tracking as a step to restrict where data was being sent from. We did not immediately see a change, and still did notice visits from Poland in the realtime reports.
In GTM, we are running Consent Mode v2, with Complianz. We do not have any trigger exclusions or explicit IP or domain rules in GTM tagging setup.
On March first, we saw 0 hits from the offending referral domains.
March 2nd and 3rd however, we still observed traffic from the referral spammer, just reducing in number. Since then, we have not. We delayed the update until today, because we are unsure if the spammer has stopped, or if we have successfully blocked it.
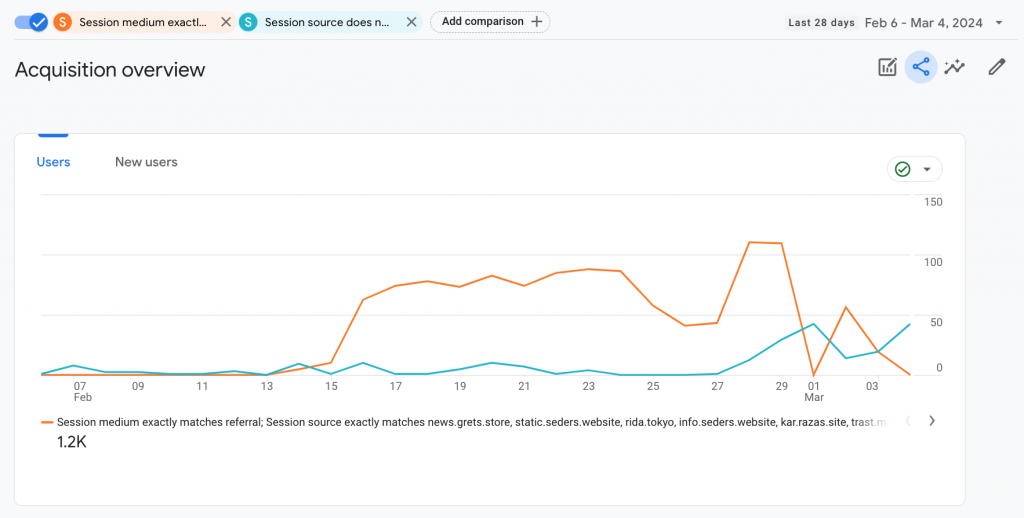
Report Available Here:
Credit to @fiskfisk on reddit for making that connection.

I tried every way and my site
[link removed]kept getting these bots. I put the ips in my server’s firewall and in 8 hours the attacks stopped.IPv4 162.243.170.83IPv4 154.211.15.85
IPv4 141.94.106.15
IPv4 139.59.230.50
IPv4 103.156.239.183
IPv4 43.156.225.179
IPv4 43.153.8.212
[link removed]